Configuring and Verifying Standard Acls
CHAPTER 1-1 Cisco IOS Software Configuration Guide Release 150SY 1 Policy-Based Routing PBR Prerequisites for PBR page 1-1 Restrictions for PBR page 1-2 Information About PBR page 1-2 Default Settings for PBR page 1-3 How to Configure PBR page 1-3 Configuration Examples for PBR page 1-7 Note For complete syntax and usage information for the. Invoking an HTTP Callout.
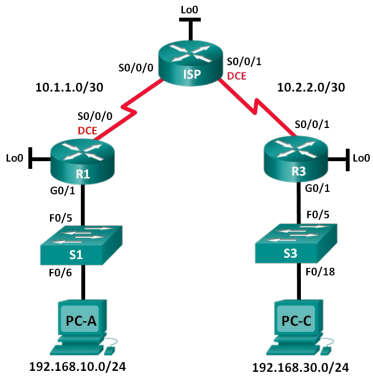
Ccna Rse 7 2 2 6 Lab Configuring And Modifying Standard Ipv4 Acl S Config Router
OSPF Overview Open Shortest Path First OSPF is a link-state routing protocol that is designed to work with large more complex networks.

. The Precision Time Protocol PTP is a protocol used to synchronize clocks in a networkWhen used in conjunction with hardware support PTP is capable of sub-microsecond accuracy which is far better than is normally obtainable with NTPPTP support is divided between the kernel and user space. OSPF uses a routing metric of. These permissions are then added to the ACL on the object.
This activity focuses on defining filtering criteria configuring standard ACLs applying ACLs to router interfaces and verifying and testing the ACL implementation. Using minimal Spring Boot configuration indicating the authorization servers issuer uri Resource Server will default to verifying the iss claim as well as the exp and nbf timestamp claims. Verifying the Configuration.
It is not able to store the time standard local time or Coordinated Universal Time UTC nor set the Daylight Saving Time DST. Packet filtering is generally accomplished by configuring Access Control Lists ACL on routers or switches. For more information see Access Control List ACL Overview and Managing ACLs Using the REST API.
The routers are already. For more information on configuring Accelerated networking see Configure a Citrix ADC VPX instance to use Azure accelerated networking. Enter the email address you signed up with and well email you a reset link.
Filtering Clients by Using an IP Blacklist. Federal Government agencies create a future-fit workforce skilled in competencies ranging from compliance to cloud migration data strategy leadership development and DEIAs your strategic needs evolve we commit to providing the content and support that will keep your workforce skilled and ready for the roles of tomorrow. Suite-B Integrity algorithm type transform configuration.
The hwclock utility saves its settings in the etcadjtime file which is created with the first change you make for example when you set the time manually or synchronize the hardware clock with the system time. To create a standard access list it uses the following syntax. Suite-B SHA-2 family HMAC variant and Elliptic Curve EC key pair configuration.
If the bucket that youre copying objects to uses the bucket owner enforced setting for S3 Object Ownership ACLs are disabled and no longer affect permissions. Avoiding HTTP Callout Recursion. Configuring Internet Key Exchange Version 2 IKEv2 feature module.
Configuring an HTTP Callout. At Skillsoft our mission is to help US. We have already learned how to use the access-list command to create a standard access list in the previous part of this tutorial.
Standard access control lists ACLs are router configuration scripts that control whether a router permits or denies packets based on the source address. As traffic enters or exits an interface firewall applies ACLs from top to bottom to each incoming packet finds matching criteria and either permits or denies the individual packets. The kernel in Red Hat Enterprise Linux includes support for PTP clocks which are.
In circumstances where validation needs to be customized Resource Server ships with two standard validators and also accepts custom OAuth2TokenValidator instances. ACL is a table of packet filter rules. OSPF is a classless routing protocol that supports VLSM and CIDR and uses the Shortest Path First SPF algorithm to calculate the best path to a network.
ESI Support for Fetching and Updating Content Dynamically. Configuring Internet Key Exchange for IPsec VPNs feature module. From VPX 1000 to VPX 10000 models you must enable Accelerated networking on Citrix ADC VPX instances to get the desired performance.
In this part lets use the ip access-list command. The ip access-list is a global configuration mode command. Access Control and Authentication.
Configuring Security for VPNs with IPsec feature module. ACL is a table of packet filter rules. Caching HTTP Callout Responses.

7 2 2 6 Lab Configuring And Modifying Standard Ipv4 Acls Youtube

9 2 2 7 Lab Configuring And Verifying Standard Acls Youtube

Pdf Lab Configuring And Verifying Standard Acls Instructor Version Topology Nguleka Edward Academia Edu
No comments for "Configuring and Verifying Standard Acls"
Post a Comment